Security Information Exchange (SIE) Valued-Added Passive DNS
Farsight Security’s Security Information Exchange (SIE) passively observes and collects unique DNS answers based on analysis of the DNS messages’ associated RRname, RRtype, Bailiwick, and Rdata. After the data is sent to SIE, it then passes through a series of processing phases, in what is called a waterfall model, to prepare for insertion to the DNSDB historical database. The SIE “Passive DNS Channels” enable customers to access, acquire, and process these incoming observations in near real-time at various phases of the processing model.
About Security Information Exchange (SIE)
The Security Information Exchange (SIE), from Farsight Security® Inc. (now a part of DomainTools), is a scalable and adaptable real-time data streaming and information sharing platform. SIE collects and provides access to more than 200,000 observations per-second of raw data from its global sensor network. Farsight also applies unique and proprietary methods for improving usability of the data, directly sharing the refined intelligence with SIE customers and DNSDB®, one of the world’s largest passive DNS (pDNS) databases.
The diverse set of data available from SIE includes the following and is relevant and useful for practitioners in various technology roles:
- Raw and processed passive DNS data
- Darknet/darkspace telescope data
- SPAM sources and URLs
- Phishing URLs and associated targeted brands
- Connection attempts from malware-infected systems (as seen by a sinkhole)
- Network traffic blocked by Intrusion Detection Systems (IDS) and firewall devices
Each unique set of data in SIE is known as a channel and the data acquired from a specific channel can be customized to meet the needs of each customer, enabling you to subscribe to and access only the channels needed to solve your problem. A channel in SIE may be the result from analyzing the data or a subset of data from other channels.
Why Passive DNS (pDNS)?
DNS is a critical component of Internet communication and almost all Internet transactions begin with a DNS query and response.
- Visiting a website? Your system uses DNS to resolve the IP address of the hostname for the website you are attempting to access.
- Sending an email? Email uses DNS to resolve the IP address of the mail exchange server your message should be delivered to.
DNS serves as early warning and detection solution for phishing, spam, malicious and suspicious behaviors, and other attacks. DNS intelligence is considered the only source of “ground truth” information for the Internet.
Passive DNS (pDNS) begins with raw DNS traffic that is observed and collected by passive DNS sensors and contributed to Farsight’s Security Information Exchange (SIE) by pDNS sensor operators. Once the data is sent to SIE, the data then passes through a series of processing phases:
- Deduplication: Channel 207, DNSDB Deduplicated Data
- Verification: Channel 208, DNSDB Verified Data
- Filtering: Channel 204, Processed DNS Data (which used by DNSDB)
The end result is the highest-quality and most comprehensive passive DNS database, DNSDB, of its kind-with more than 100 billion unique DNS resource records since 2010.
Farsight Security’s mission is to make the Internet a safer place. We provide security solutions that empower customers with meaningful and relevant intelligence. This information provides customers with insights about the network configuration of a threat and the surrounding network on the Internet for improving the value and impact of threat intelligence and research.
The Security Information Exchange (SIE), from Farsight Security Inc., is designed with privacy in mind. The passive DNS (pDNS) sensors do not collect Personally Identifiable Information (PII) from client resolvers (also known as stub) by deliberately collecting between recursive resolvers and authoritative servers.
The data from SIE enables security professionals to accurately identify, map, and protect their networks from cybercriminal activity by providing global visibility. It provides immediate access to a real-time global sensor network without the need to develop or deploy your own data collection infrastructure.
About SIE Passive DNS Channels
Passive DNS (pDNS) begins with raw DNS traffic that is observed and collected by passive DNS sensors and contributed to Farsight’s Security Information Exchange (SIE) by pDNS sensor operators. Once the data is sent to SIE, the data then passes through a series of processing phases, starting with deduplication.
Three SIE channels are available that allow access to DNS intelligence observed at different phases of the “waterfall model” processing. These channels are:
| Channel | Name | Description |
| 204 | Processed DNS Data | Passive DNS observations that passed through the waterfall processing phases. Filtering removes domains related to some wildcards, DNS VPNs, DNS block lists, and auto-generated names from IP addresses. |
| 207 | DNSDB Deduplicated Data | Passive DNS observations that passed through the deduplication phase and will be sent to the verification phase of the waterfall. |
| 208 | DNSDB Verified Data | Passive DNS observations that passed through the verification phase and will be passed on to the filtering phase. |
Data is processed by Security Information Exchange (SIE) in what is called a waterfall model. The following diagram can help inform and guide you in understanding the data that is available from the various SIE DNS channels. Farsight’s Solution Architect’s (SAs) are happy to discuss criteria for selecting the appropriate SIE Channels with customers.
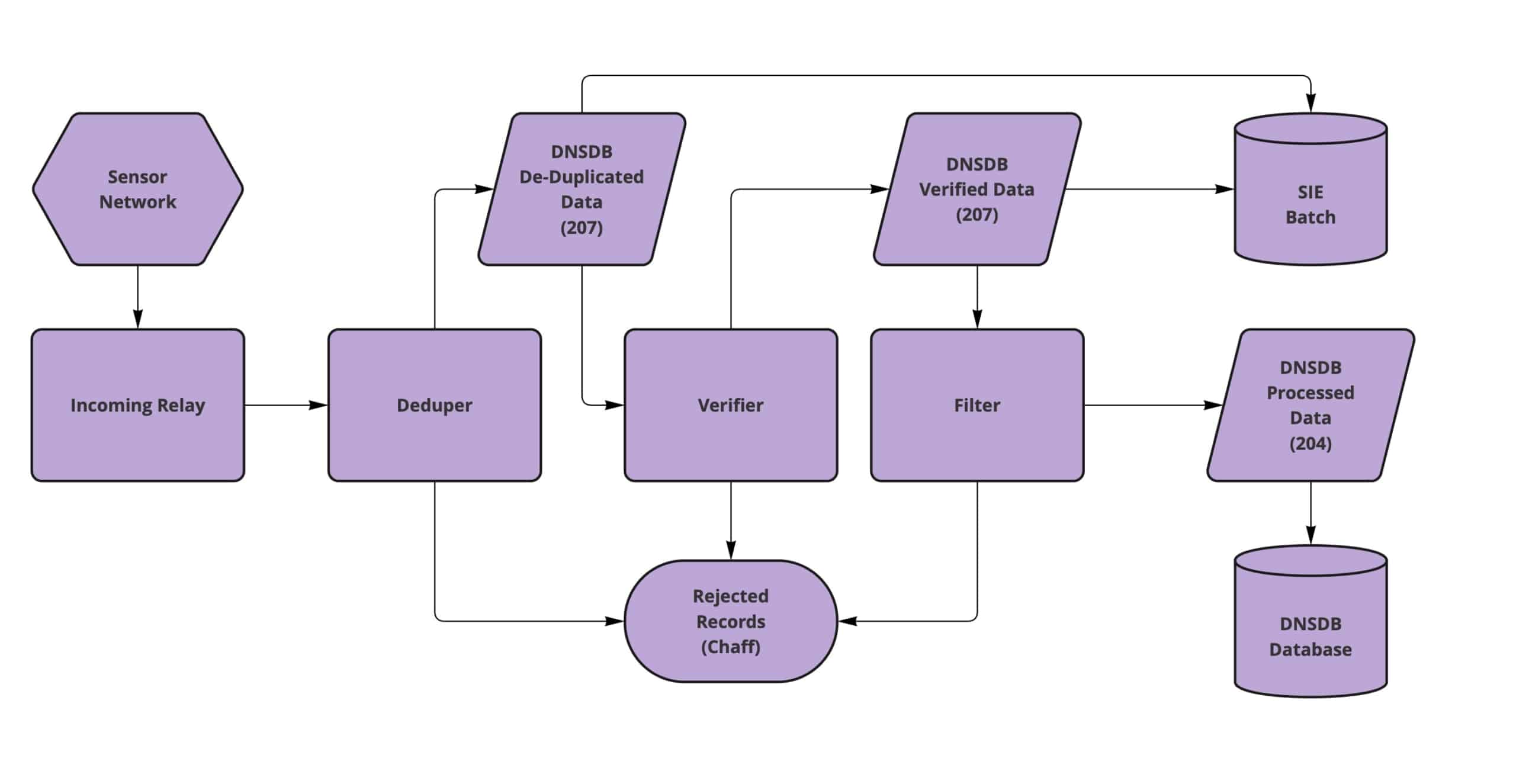
For more information on these terms, please reference the ISC Passive DNS Architecture document.
There are articles with more details about Passive DNS (pDNS) listed in the Additional Information section below. For more info on RRname, RRtype and Rdata, see What is a Bailiwick?
SIE Channel 207 (DNSDB De-duplicated Data) — Deduplication Phase
Farsight’s passive DNS (pDNS) solution observes and collects unique DNS answers based on analysis of the associated RRname, RRtype, RData, and bailiwick. Since the raw DNS data includes many duplicate answers for common DNS questions, that may be observed many times per-second, SIE deduplicates the data in the first phase of the waterfall model.
The deduplication phase performs data reduction and exports the unique DNS records with counts for the number of times each unique DNS answer was observed in the data.
However, some types of DNS data are also filtered at this state, such as DNS messages that have a bad checksum value or data that has been delayed for more than an hour. These records are discarded. To see current channel traffic volumes and service options for accessing it, please see the Security Information Exchange (SIE) Channel Guide.
| Channel Name | DNSDB De-duplicated Data |
| Description | Passive DNS observations after the deduplication processing phase and immediately prior to the verification phase. |
| Channel Number | 207 |
| Schema | SIE:dnsdedupe |
SIE Channel 208 (DNSDB Verified Data) — Verification Phase
Rogue, malicious, or misconfigured name servers may respond with misleading resource record information for a domain or domains. The verification phase ensures that only bailiwick-appropriate DNS data is passed on to Channel 208, DNSDB Verified Data. DNS data that fails bailiwick verification are discarded. To see current channel traffic volumes and service options for accessing it, please see the Security Information Exchange (SIE) Channel Guide.
| Channel Name | DNSDB Verified Data |
| Description | Passive DNS observations after the verification processing phase and prior to filtering. |
| Channel Number | 208 |
| Schema | SIE:dnsdedupe |
For more information on bailiwicks and how they are used in DNSDB, see What is a Bailiwick.
SIE Channel 204 (Processed DNS Data) — Filtering Phase
The next phase is filtering and the final phase in the waterfall model processing. In this phase, various categories of DNS data are filtered, which may including the following:
- Dynamic addresses, which is rarely of interest to passive DNS (pDNS) users
- encrypted DNS tunneling traffic
- DNS-as-general-purpose-database traffic
DNS records that are not filtered are sent to Channel 204, Processed DNS Data, which is the channel also used by DNSDB. To see current channel traffic volumes and service options for accessing it, please see the Security Information Exchange (SIE) Channel Guide.
| Channel Name | Processed DNS Data |
| Description | Passive DNS observations after deduplication, verification, and filtering. |
| Channel Number | 204 |
| Schema | SIE:dnsdedupe |
Using Passive DNS Channel Data
Data acquired from Channel 204, 207, or 208 is returned in NMSG format for all access methods. NMSG is an adaptable container format that allows for consistent or variable message types.
The nmsgtool program is a tool for acquiring a variety of different inputs,
like data streams from the network, capturing data from network interfaces,
reading data from files, or even standard input and making NMSG payloads
available to one or more outputs. The nmsgtool program can acquire data from
SIE Channel 220 and convert it to a ND-JSON (newline-delimited JSON) text format
for display or additional processing and analysis. nmsgtool is a program
written by Farsight and released as open source.
See the following pages for instructions on how to install software packages for a specific distribution.
- Security Information Exchange (SIE) on Debian
- Security Information Exchange (SIE) on CentOS 6 / RHEL 6
- Security Information Exchange (SIE) on FreeBSD
After data for Channel 220 has been acquired, written, and saved to a file, you
need to decode it to ND-JSON using nmsgtool. The [-r pdns-data.nmsg] option
tells nmsgtool to read binary NMSG data from a file, [-c 1] limits the
output to single NMSG payload, and [-J -] displays the record in ND-JSON
format to stdout, which is typically the screen.
$ nmsgtool -r pdns-data.nmsg -c 1 -J - (returned ND-JSON record)Once the data has been formatted to ND-JSON, a record from the DNS Changes channel will look similar to the following. The following output can be sent to another tool for additional processing.
{"time":"2020-04-06 21:48:59.039279480","vname":"SIE","mname":"dnsdedupe",
"message":{"type":"EXPIRATION", "count":2,"time_first":"2020-04-06 18:47:22",
"time_last":"2020-04-06 18:47:22","bailiwick":"example.com.",
"rrname":"www.example.com.",
"rrclass":"IN","rrtype":"CNAME","rrttl":3600,"rdata":["dns.example.com."]}}If you want to display a pretty-printed output of ND-JSON formatted records, we recommend using jq, a lightweight and flexible command-line JSON processor.
The open source software package is available on Debian and can be installed using $ sudo apt-get install jq. The output from nmsgtool in JSON format [-J -] can be piped to
jq using the following:
$ nmsgtool -r pdns-data.nmsg -c 1 -J - | jq -r '.'
{
"time": "2020-04-06 21:48:59.039279480",
"vname": "SIE",
"mname": "dnsdedupe",
"message": {
"type": "EXPIRATION",
"count": 2,
"time_first": "2020-04-06 18:47:22",
"time_last": "2020-04-06 18:47:22",
"bailiwick": "example.com.",
"rrname": "www.example.com.",
"rrclass": "IN",
"rrtype": "CNAME",
"rrttl": 3600,
"rdata": [
"dns.example.com."
]
}
}Data Format for SIE Passive DNS Channels — 204, 207, and 208
The SIE NMSG dnsdedupe schema is a DNS Query and Response resource record (RR) schema that observes and collects data returned from a query. You can find the definition for the schema here:
The data available from these channels contain NMSG SIE:dnsdedup type messages that include the following fields:
| KEY | VALUE |
|---|---|
| time | Time when hostname was first observed in Channel 204. |
| vname | Vendor Name, SIE. |
| mname | Message type, dnsdedupe. |
| group | Reason DNS message was rejected. |
| message | Embedded JSON record describing the observed DNS Query and Response RR. |
The embedded NMSG message payload is JSON formatted and includes the following fields:
| KEY | VALUE |
| type | Types are INSERTION, EXPIRATION, or CHAFF. |
| count | Number of times an RRset was observed since the last message was sent to the channel. |
| time_first1,2 | Indicates first time the RRset was observed by pDNS. |
| time_last1,2 | Indicates last time the RRset was observed by pDNS. |
| response_ip3 | IP address of the name server replying to the query. |
| rrname | Domain name or hostname of the query observed by pDNS or extracted from a zone file import. |
| rrclass | RR CLASS is always “Internet (IN)“, which is decimal value “1“. |
| rrtype | RR TYPE describes the type of RR, e.g., A(1), NS(2), CNAME(5) |
| rrttl | Time to live (TTL) of the RR. |
| rdata | Data that describes the RR type (may repeat). |
| bailiwick4 | The domain under which the RRset answer was given5. |
1 Unix epoch timestamps with second granularity in UTC.
2 Field is not present if the RRset was only observed from a zone file import.
3 Field always exists in Channel 207 and optional in Channels 204 and 208. If the answer was returned from one (1) name server, it lists bailiwick instead of response_ip.
4 Field always exists in channels 204 and 208. It is not returned in Channel 207.
5 For example, an authoritative generic TLD (gTLD) name server for “com.” may respond with different answers for the same query than the authoritative name servers for “farsightsecurity.com.” would respond with.
Understanding Passive DNS INSERTION & EXPIRATION Messages
DNS data sent to channel DNSDB Deduplicated Data (207), DNSDB Verified Data (208), or Processed DNS Data (204) will be either INSERTION or EXPIRATION type messages.
To understand what INSERTION and EXPIRATION mean, we need to discuss how deduplication is implemented in SIE. During processing, the waterfall model maintains a cache table of observed RRsets as a large ring buffer in memory.
When DNS data is received by SIE, the cache table is checked to see if the RRset
already exists. If the RRset exists in the cache table, the cache entry’s count
is incremented and the time_last field is updated, and the record discarded as
a duplicate. If the RRset does not exist in the cache table, the record is
inserted into the cache, and an “INSERTION” record is sent from the
deduplicator to the next phase of processing. This causes the oldest record in
the ring buffer to be expired from the cache table, and an “EXPIRATION” record
is sent from the deduplicator to document the removal. These records are
broadcast to the DNSDB Deduplicated Data (207) channel and for the
verification phase of the waterfall mode.
If you are primarily interested when an RRset is first observed, you can focus on “INSERTION” records and if you are interested in how often an RRset is observed, you should monitor “EXPIRATION” records.
Example Message — INSERTION Record
The time_first and time_last fields for INSERTION records are always the
same and the count is always 1. In the following example, the query was
received from IP address 10.10.10.10 (which is acting as the authoritative name
server for com.) and the message indicates an SOA record was observed in the
response. rrttl displays Time to Live (TTL) value for the record that would
be used when caching the data, and rdata is the data returned for the query.
{
"time": "2020-04-06 22:39:55.429865036",
"vname": "SIE",
"mname": "dnsdedupe",
"message": {
"type": "INSERTION",
"count": 1,
"time_first": "2020-04-06 22:38:48",
"time_last": "2020-04-06 22:38:48",
"response_ip": "10.10.10.10",
"bailiwick": "com.",
"rrname": "com.",
"rrclass": "IN",
"rrtype": "SOA",
"rrttl": 86400,
"rdata": [
"dns.example.com. dns2.example.com. 1586212699 1800 900 604800 86400"
]
}
}Example Message — EXPIRATION Record
The following example message is for a AAAA resource record. The data
returned in the rdata field are the IPv6 addresses for the domain in therrname field, which is www.example.com.. With the site acting as its own
authoritative name server in the bailiwick. Since count is 1,time_first will match time_last, indicating only one query was seen before
record expired from the hash table. If value of count was more than 1,time_last may or may not be the same as time_first.
{
"time": "2020-04-06 22:39:57.420893762",
"vname": "SIE",
"mname": "dnsdedupe",
"message": {
"type": "EXPIRATION",
"count": 1,
"time_first": "2020-04-06 19:32:42",
"time_last": "2020-04-06 19:32:42",
"bailiwick": "www.example.com.",
"rrname": "www.example.com.",
"rrclass": "IN",
"rrtype": "AAAA",
"rrttl": 120,
"rdata": [
"2001:db8::1"
"2001:db8::2"
"2001:db8::3"
"2001:db8::a"
"2001:db8::b"
"2001:db8::c"
]
}
}DNS Terminology: RRname (RRset), Rdata, RRtype and Bailiwick
There are DNS terms used in this document that my be unfamiliar to the reader.
Definitions and links to additional information for these terms follows:
- RRname: Also known as the question or “RRset“, refers to the
left-sideof a resource record in a DNS response and contains the owner name, TTL, CLASS, TYPE and RDATA. An RRset contains one or more resource records with the same owner name, class, type, rdata, usually the same TTL, and observed at the same time. - Rdata: Also known as the answer or “record data“, refers to the
right-sideof a resource record in a DNS response. - RRtype: This field in the DNS resource record specifies the type of data that is being returned. Common RRtype values include A (host address), AAAA (IPv6 host address), CNAME (Canonical name), and NS (Name server). See A Quick Overview of the Top Seven DNS Record Types for additional information.
- Bailiwick: DNS data is considered “in bailiwick” if the resource record being returned is the response from a name server that is known to be responsible for answering with authoritative information about that domain. See What is a Bailiwick? for additional information.
Example DNS Resource Record: RRname, RRclass, RRtype, and Rdata
In the example DNS resource record that follows, RRname (left-side) refers
to www.farsightsecurity.com and Rdata (right-side) refers to 66.160.140.81 or the IP address. Rdata can also refer to a Fully Qualified
Domain Name (FQDN) such as info.farsightsecurity.com. See RRset and Rdata Demystified for additional information.
| RRname/RRset (Left-Side) | RRclass | RRtype | Rdata (Right-Side) |
|---|---|---|---|
| www.farsightsecurity.com | IN | A | 66.160.140.81 |
SIE Access Methods
Data from SIE can be accessed and acquired using the following methods:
- Direct Connect: Connect a system to the SIE network. This 1.) requires a server to be installed in a data center where Farsight has a point of presence, and 2.) then ordering a network cross connect between your server and the SIE network. Customers can optionally, and prefer to, lease a blade server from Farsight.
- SIE Remote Access (SRA): Remotely connect to the SIE network using an encrypted tunnel from your workstation or a server in your local data center.
- SIE Batch: Provides on-demand access for downloading data from SIE channels using a RESTful API or web-based interface. You select the channel and duration of time you are interested in, and then download the data for analysis. The duration of available data is dependent on the channel, but is typically the most recent 12-18 hours.
For additional information about SIE access methods, please see the SIE Technical Overview document.
Direct Connect
SIE Direct Connect allows a customer to physically connect a server to the Farsight SIE network for maximum data throughput. This can be done in one of two ways:
- Blade Server: Pre-configured blade servers co-located in one of Farsight’s data centers that can be leased by customers for direct access to SIE channels.
- Customer Server: Customer (owned, managed, and operated) servers that can be installed in one of Farsight’s data centers and physically connected to the SIE network with a network cross-connect.
If a blade server is leased from Farsight, it will be pre-installed with the essential software components needed to acquire, process, compress, buffer, and transfer data from SIE channels to the customer’s data center for additional analysis, enrichment, and storage.
If a customer uses their own server, an order can be submitted for a cross-connect to the SIE switches hosted at select Equinix data centers (Ashburn DC3 and Palo Alto SV8). An FSI account manager can help guide cross-connect provisioning details, hosting, or colocation options.
For additional information about SIE connection methods, please see the SIE Technical Overview document. A Farsight’s sales representatives is happy to share a copy of this document with you. This will help inform and guide you in understanding which connection method will work best for you.
SIE Remote Access (SRA)
SIE Remote Access (SRA) enables a customer to remotely connect to the Security Information Exchange (SIE) from anywhere on the Internet. SRA provides access to SIE channel data on customer’s local servers, allowing their analysis and processing systems to be located in their own data centers rather than physically co-located at a Farsight’s data center.
Due to the technical limitations of transporting high bitrate SIE channels across the Internet, the SRA access method is not available for all SIE channels. Please reference the SIE Channel Guide for channels that can be accessed using SRA.
SRA uses the Advanced Exchange Access (AXA) transport protocol which enables SRA sessions to perform the following:
- Select which SIE channel or channels to monitor and acquire data from
- Define user-specified search or filtering criteria to match IP or DNS traffic
- Control rate-limits and other AXA parameters
The streaming search and filtering capabilities of AXA enables SRA to access and acquire meaningful and relevant data from SIE while avoiding the costs of transporting enormous volumes of data across the Internet.
Note: For high volume channels accessed using SRA, it is expected that customer’s will specify a search or filter for IP addresses and DNS domain names or hostnames of interest. The SRA service will only collect and send data matching the specified criteria across the Internet to the customer.
SIE Batch
SIE Batch provides on-demand access for downloading data from SIE channels using a RESTful API or web-based interface. You select the channel and duration of time you are interested in, and then download the data for analysis. The duration of available data is dependent on the channel, but is typically the most recent 12-18 hours. SIE Batch allows you to acquire data from SIE channel using two (2) methods:
- API: Allows you to write tools to programmatically download data from SIE channels for analysis.
- Interactively: Web-based interface to the API that enables you to select and download SIE channel data on-demand.
Advanced Exchange Access Middleware Daemon (AXAMD)
Farsight also provides a RESTful middleware layer in front of its AXA service. This service is called the AXA Middleware Daemon (AXAMD) and provides a RESTful capability that adds a streaming HTTP interface on top of the AXA toolkit. This enables web-application developers to interface with SIE using SRA. Farsight also published a command line tool and Python extension library called axamd_client. This toolkit is licensed under the Apache 2.0 license.
The Advanced Exchange Access (AXA) toolkit contains tools and a C library to bring Farsight’s real-time data and services directly from the Farsight Security Information Exchange (SIE) to the customers network.
Advanced Exchange Access Middleware Daemon (AXAMD) is a suite of tools and library code to bring Farsight’s real-time data and services directly from the Farsight Security Information Exchange (SIE) to the customers network.
Due to the technical limitations of transporting high bitrate SIE channels across the Internet, the AXAMD access method is not available for all SIE channels.
Additional Information
- ISC Passive DNS Architecture
- Passive DNS – Common Output Format
- SIE User Guide
- SIE Channel Guide
- What is a Bailiwick?
- RRset and Rdata Demystified
- A Quick Overview of the Top Seven DNS Record Types
- SIE:dnsdedupe DNS Query and Response RR Deduplication schema
jqa lightweight and flexible command-line JSON processor- Description of JSON Lines text format (aka ND-JSON)

